Can Wireshark Read Https in Monitor Mode
Then you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it'due south as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a telephone is running in real fourth dimension.
While using an encrypted network is ameliorate than using an open ane, the advantage disappears if the attacker is on the same network. If someone else knows the password to the Wi-Fi network you are using, it's easy to come across what you're doing at that moment using Wireshark. Information technology can allow an attacker to create a list of every app running on the device existence targeted and zippo in on apps that might exist vulnerable.
Decrypting Encrypted Packets
When you use a Wi-Fi network that uses WPA2 encryption, the security of your session is based on ii things. The beginning is the password that'south used to generate a much longer number, a PSK or pre-shared key. The 2d is the actual handshake itself, which has to happen to institute a connexion. If an attacker has the PSK to the Wi-Fi network and either observes you lot join the network or kicks you off for a moment, they can decrypt your Wi-Fi traffic to see what you're doing.
- Don't Miss: Detect Script-Kiddie Wi-Fi Jamming with Wireshark
The content of HTTPS websites won't be able to be seen, but any plain HTTP websites you visit or whatever insecure HTTP requests apps on your phone makes are in obviously view. This may not seem similar a big deal, only in only lx seconds, it'southward easy to learn a lot about the type of device nosotros're monitoring and what exactly is running on it. Too, DNS requests to resolve the domains that apps need to talk to in guild to work are easy to come across, identifying which apps and services are active.
How It Works
To pull off this assault, a few conditions need to be met. First, we demand the countersign, we need to be in proximity to the victim so nosotros can tape traffic, and we demand to exist able to kick the targeted device off the network or wait for them to reconnect. We'll open Wireshark and access the carte to decrypt Wi-Fi packets, add the PSK to enable decryption, and wait for EAPOL packets from the targeted device connecting to the network.
To get a feeling for what the targeted device is up to, nosotros'll be using capture filters to highlight DNS and HTTP packets we're looking for. To see a complete list of every domain the device has resolved, we can also look at a summary of resolved domains later the capture is complete. We can use this information to easily pick autonomously which services are running, fifty-fifty if they're but running in the background and the app hasn't been running in quite some time.
- Don't Miss: Intercept Images from a Security Camera Using Wireshark
What You'll Need
To do this, you'll need a wireless network adapter carte du jour capable of wireless monitor mode. Yous can check out our guides on selecting one that'southward Kali-uniform and supports monitor manner.
- More than Info: Purchase the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
Side by side, yous'll demand an iOS or Android smartphone connected to the Wi-Fi network you're monitoring. You can practice this on an open Wi-Fi network to see what you're supposed to see, as sometimes decryption may not work the first time. Yous'll also demand to know the password and network proper noun of the Wi-Fi network you desire to monitor. This will permit yous to calculate the pre-shared primal, allowing us to decrypt the traffic in realtime.
Stride 1: Download Wireshark & Connect to the Wi-Fi Network
Download and install Wireshark if information technology's not already installed, and connect to the Wi-Fi network your target is on. If you programme to use a PSK rather than a network key, you should calculate information technology using the Wireshark tool before doing and then, because you may not be able to access the internet during the capture, depending on your card.
Once you have Wireshark downloaded, open it, and then have a look at your network interfaces. Before nosotros start capturing, we'll need to prepare a few things upward to make sure the card is capturing in the correct mode.
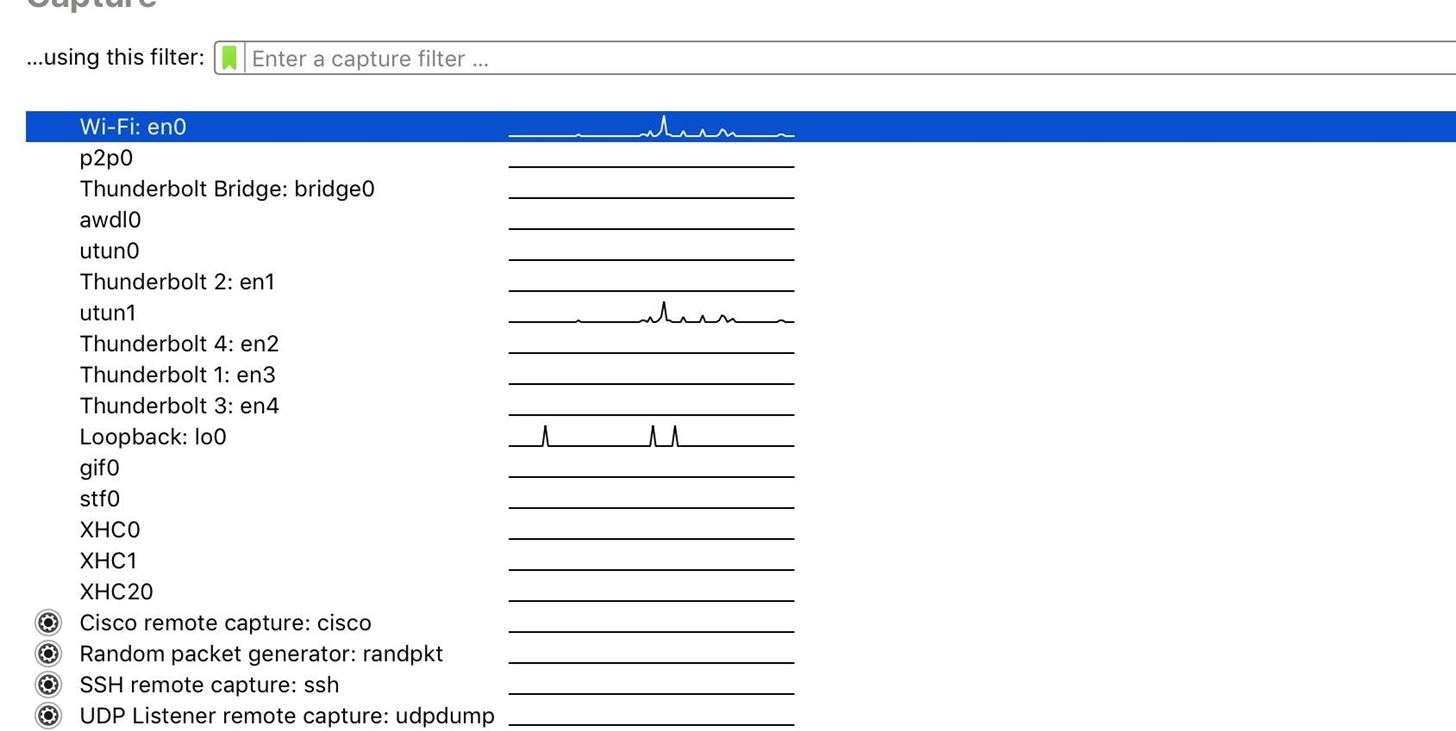
Footstep two: Set up Up Wireshark for Capturing
Nether the Wireshark bill of fare option, click on the gear-shaped "Capture options" menu.
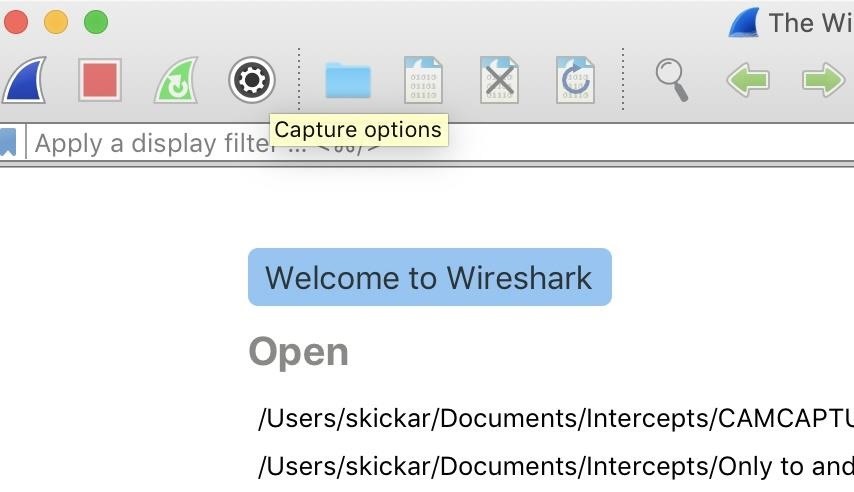
That will open the Capture Interfaces window, as seen below.
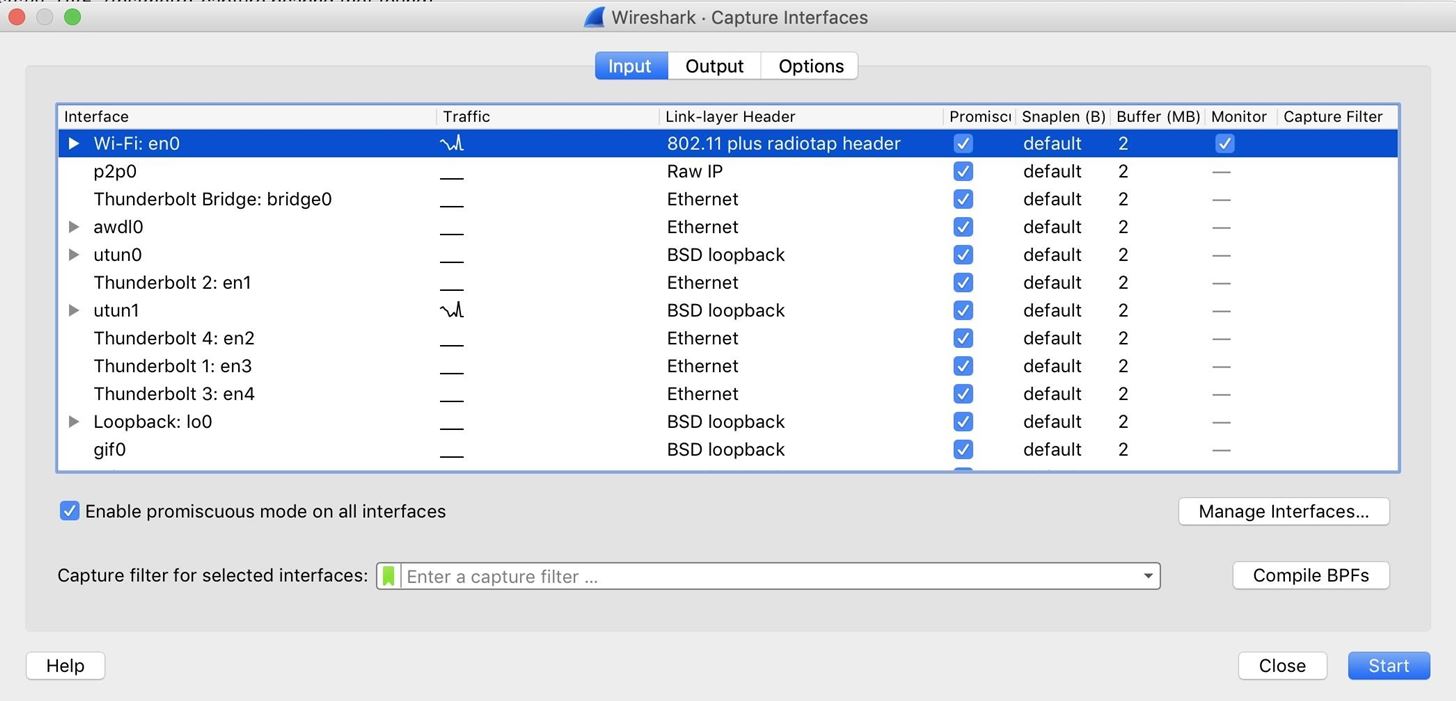
Step iii: Begin the Network Capture & Scan for EAPOL Packets
If you're not continued to the network your target is on, then you won't exist able to see whatever packets because you might exist on some other random aqueduct. Wireshark can't actually change the channel that the wireless network adapter is on, so if you're not getting annihilation, that could be why.
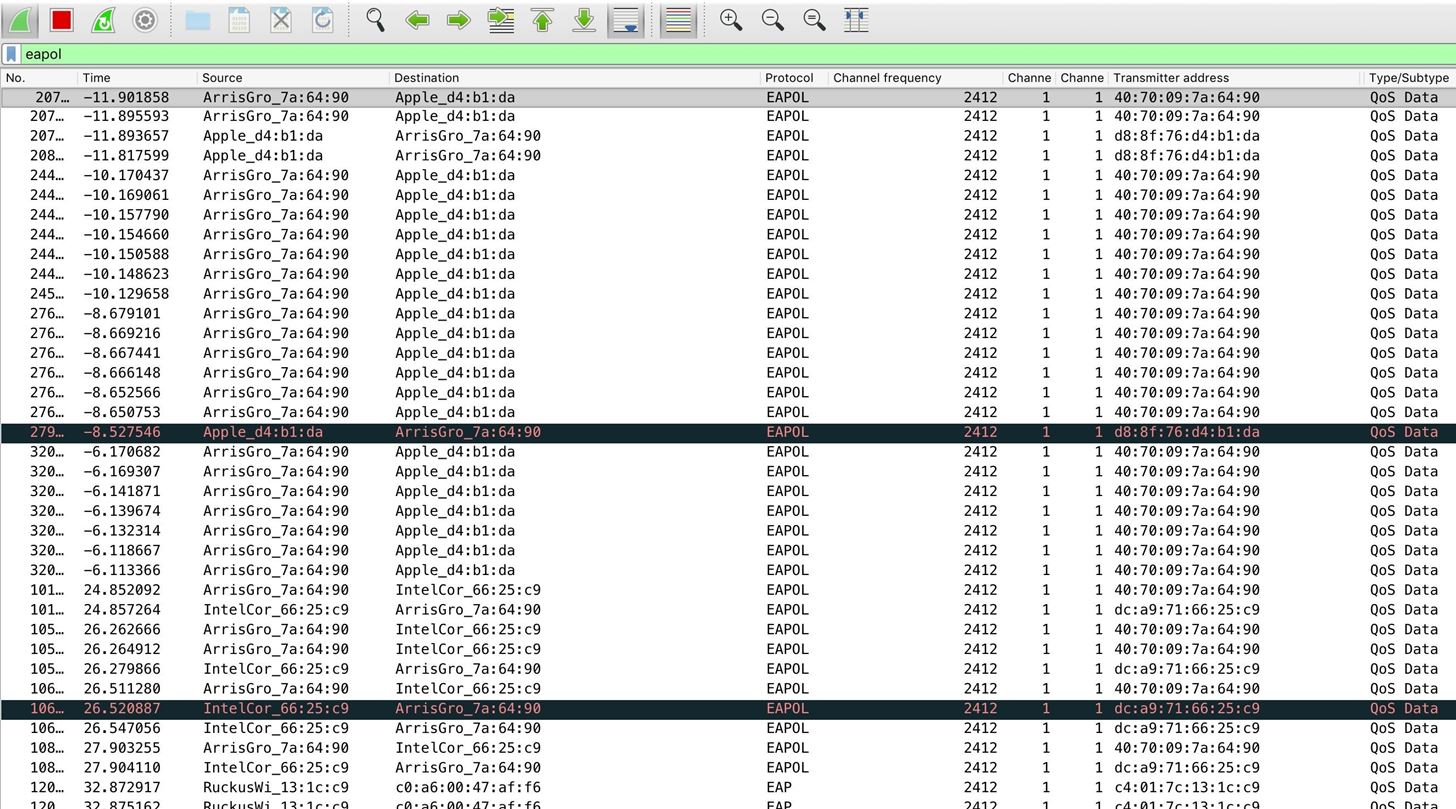
Pace 4: Decrypt Traffic with the Network PSK
At present that we take handshakes, we can decrypt the conversation from this point onwards. To practice then, we'll need to add the network password or PSK. Go to the "Wireshark" drop-down menu and select the "Preferences" selection. In one case selected, click on "Protocols."
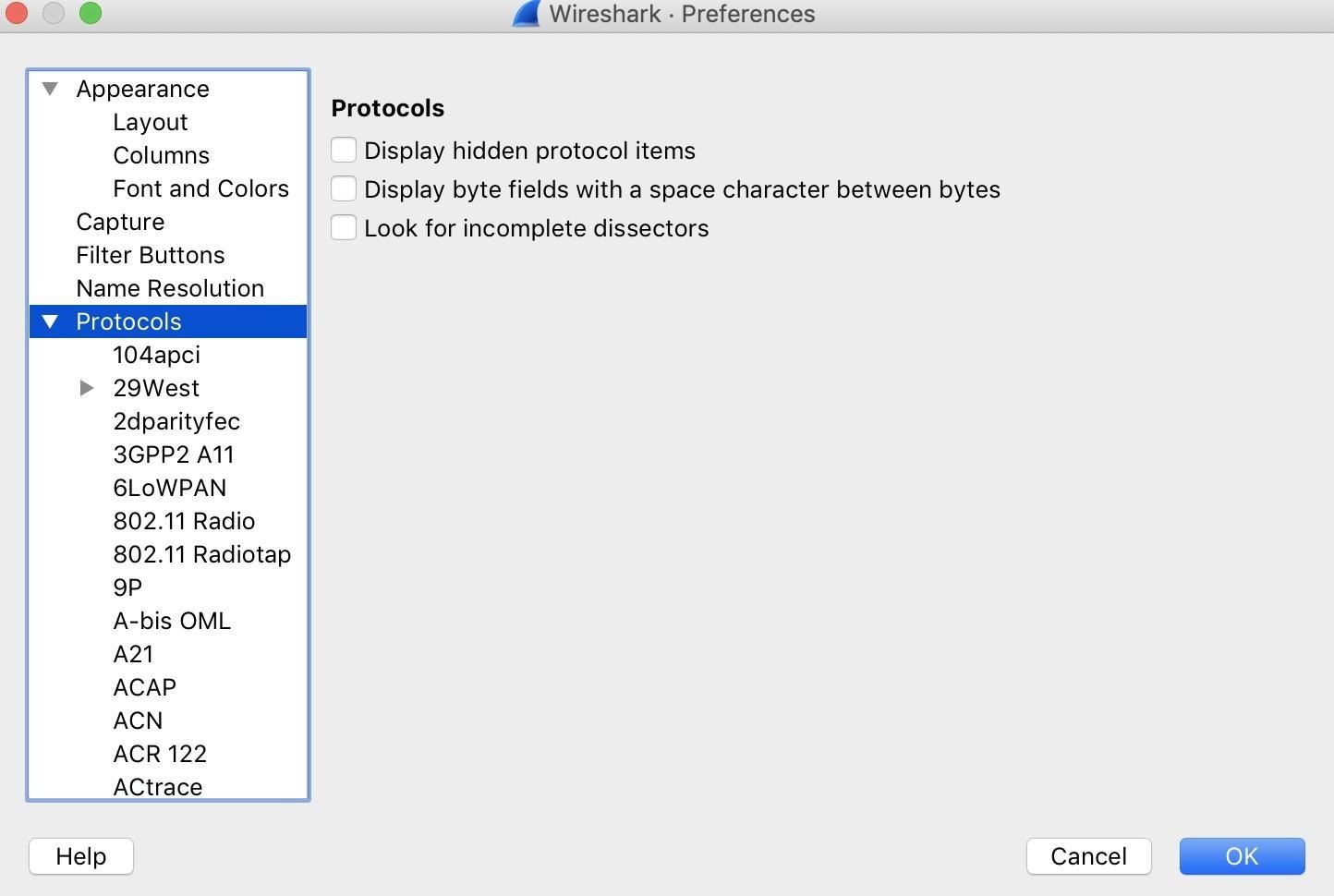
Under Protocols, select "IEEE 802.xi," and then click "Enable decryption." To add the network key, click "Edit" next to "Decryption keys" to open the window to add together passwords and PSKs.
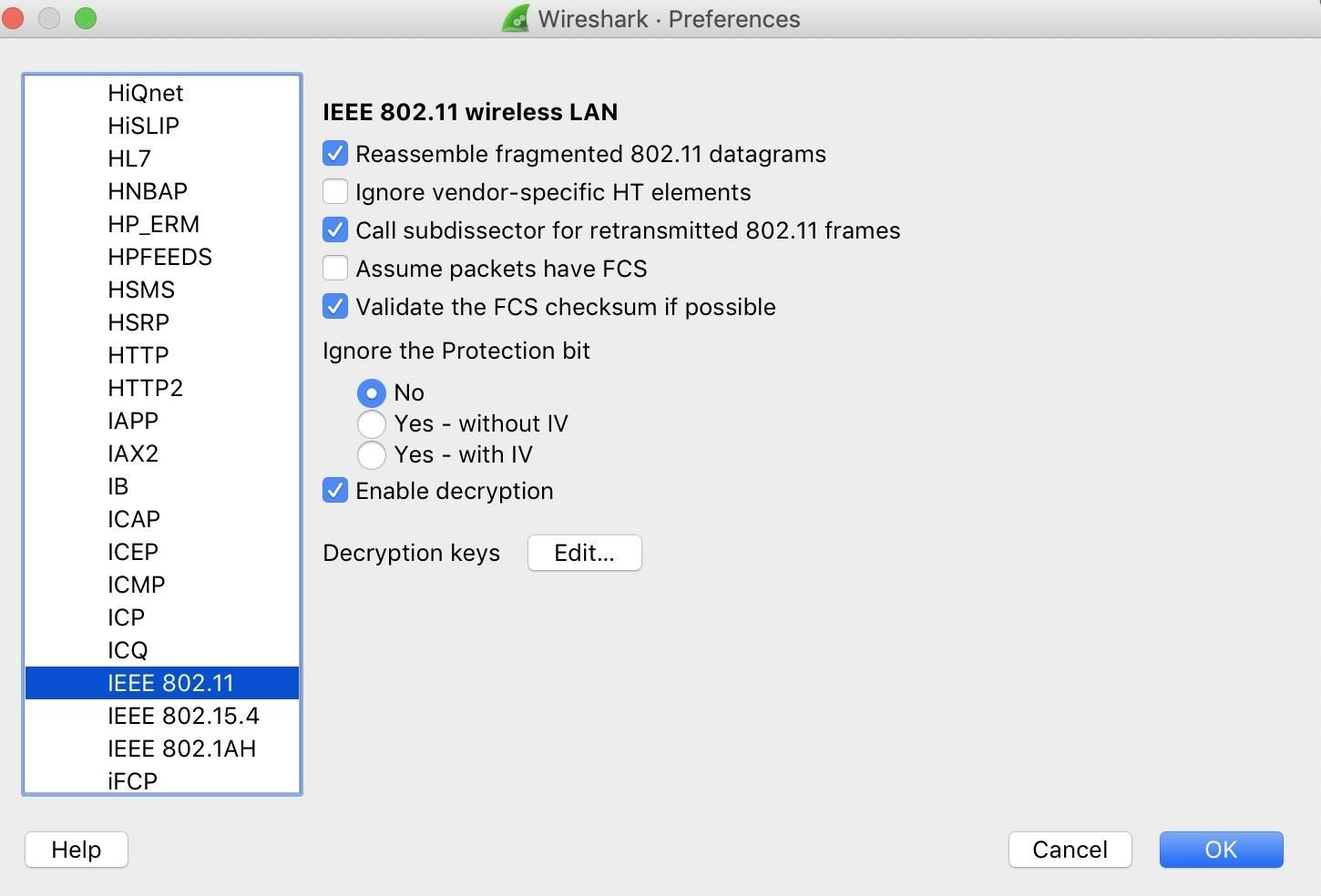
Select "wpa-psk" from the menu, and so paste in your key. Hit Tab, and then save by clicking "OK."
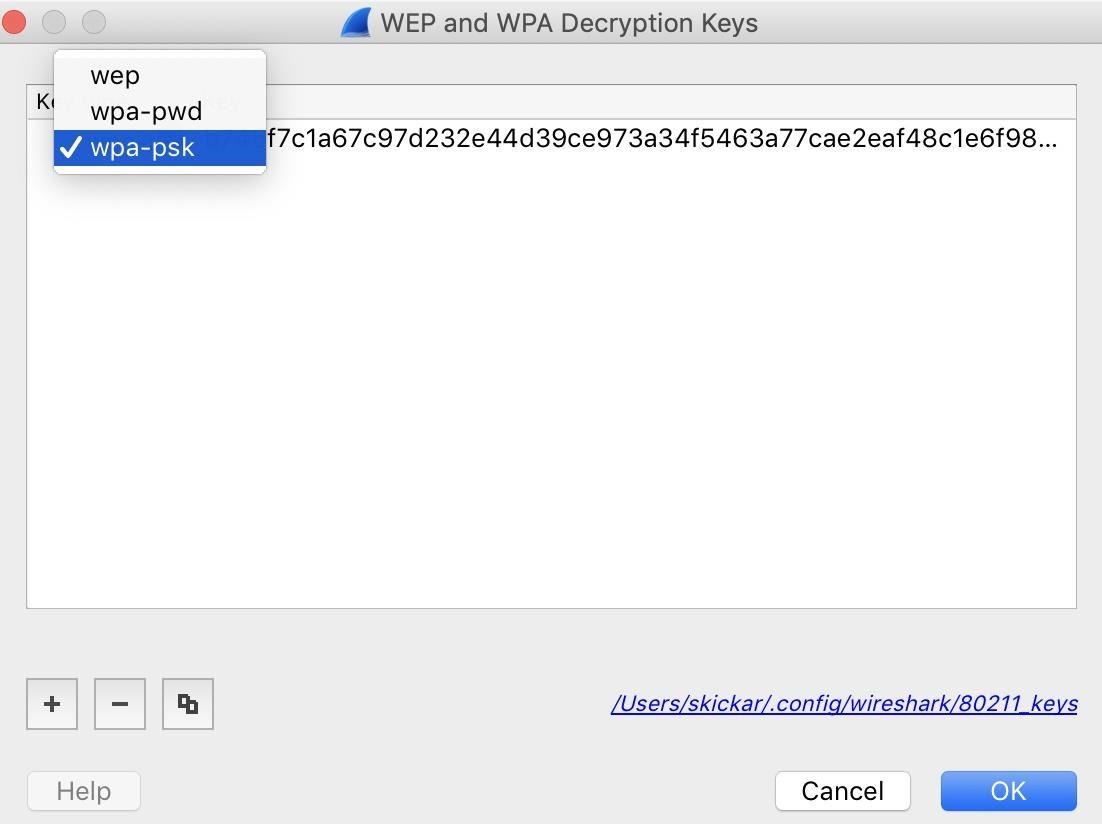
One time this is complete, click "OK" on the Preferences menu, and Wireshark should rescan all the captured packets and attempt to decrypt them. This may not piece of work for a diverseness of reasons. I was able to get it to work most of the fourth dimension by ensuring I had a good handshake (EAPOL) and switching dorsum and forth between using a network countersign and a PSK. If information technology works, we can movement on to the step of analyzing the traffic to choice out apps in use.
Step 5: Scan for DNS & HTTP Packets
Now that we accept stripped away the protection around the traffic, Wireshark tin can decrypt them and tell us what the devices on this Wi-Fi network that we have handshakes for are doing in real fourth dimension.
i. DNS Requests
To see interesting packets, we'll start with DNS requests. DNS requests are how apps make certain the IP addresses they are supposed to connect to haven't changed. They'll exist directed to domain names that normally accept the name of the app in them, making it niggling to meet which app is running on the iPhone or Android phone and making the requests.
- Don't Miss: Use Driftnet to Come across What Kind of Images Your Neighbor Looks At
To see these requests, we'll be using two capture filters, dns and http, which will prove us the most obvious fingerprints that an app leaves over Wi-Fi. First, type dns into the capture filter bar and hit Enter. If this doesn't work, try switching between a PSK and password a few times. It sucks, but sometimes it will start working.
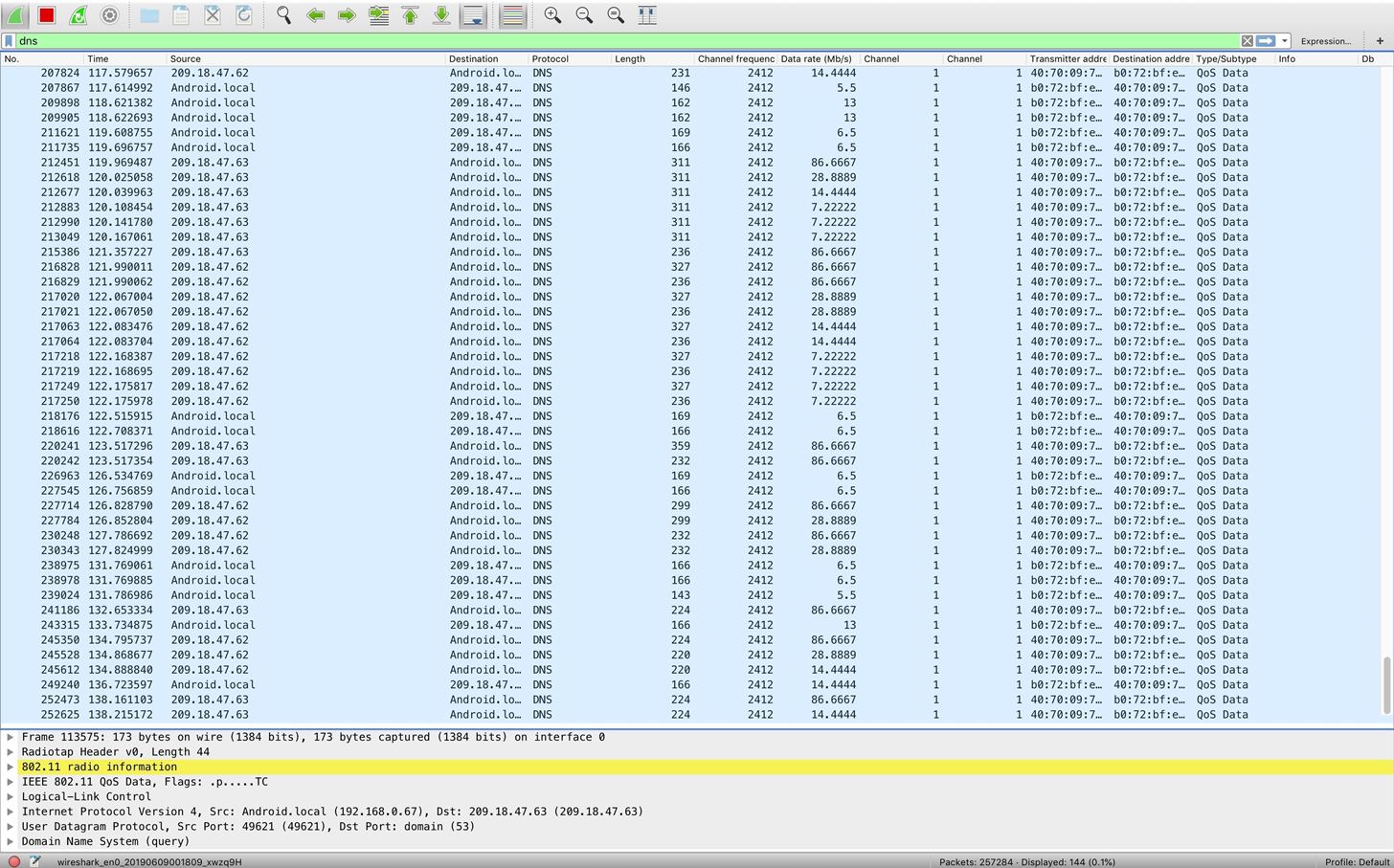
If your target is feeling lonely, y'all might run across the response below. Tinder calls the Tindersparks.com domain, as well as a lot of other services. This request is one of the most obvious.
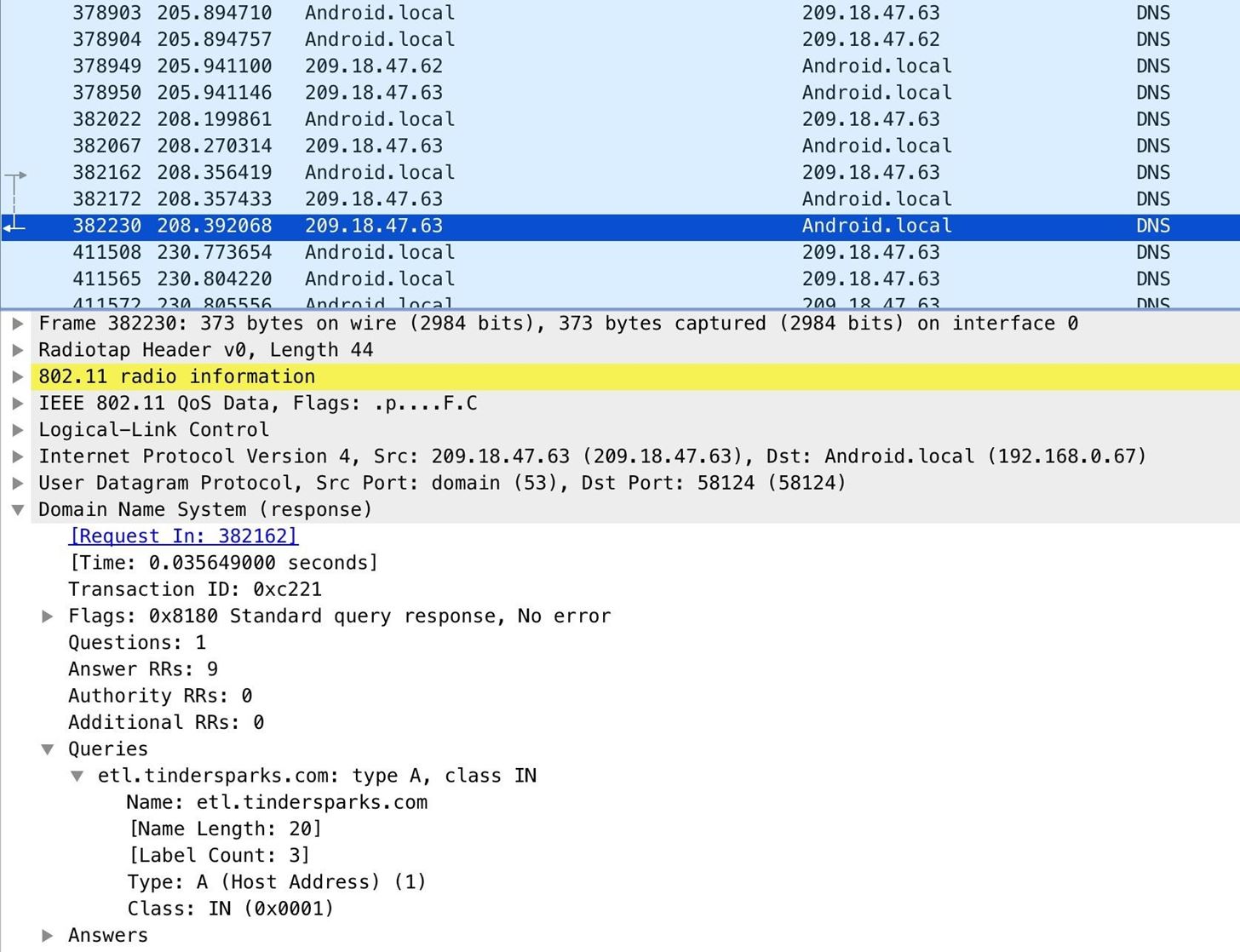
While using Indicate is a good idea, using it with a VPN is a better idea. The reason? Even opening Signal creates the substitution below, conspicuously identifying that the user is communicating with an encrypted messenger.
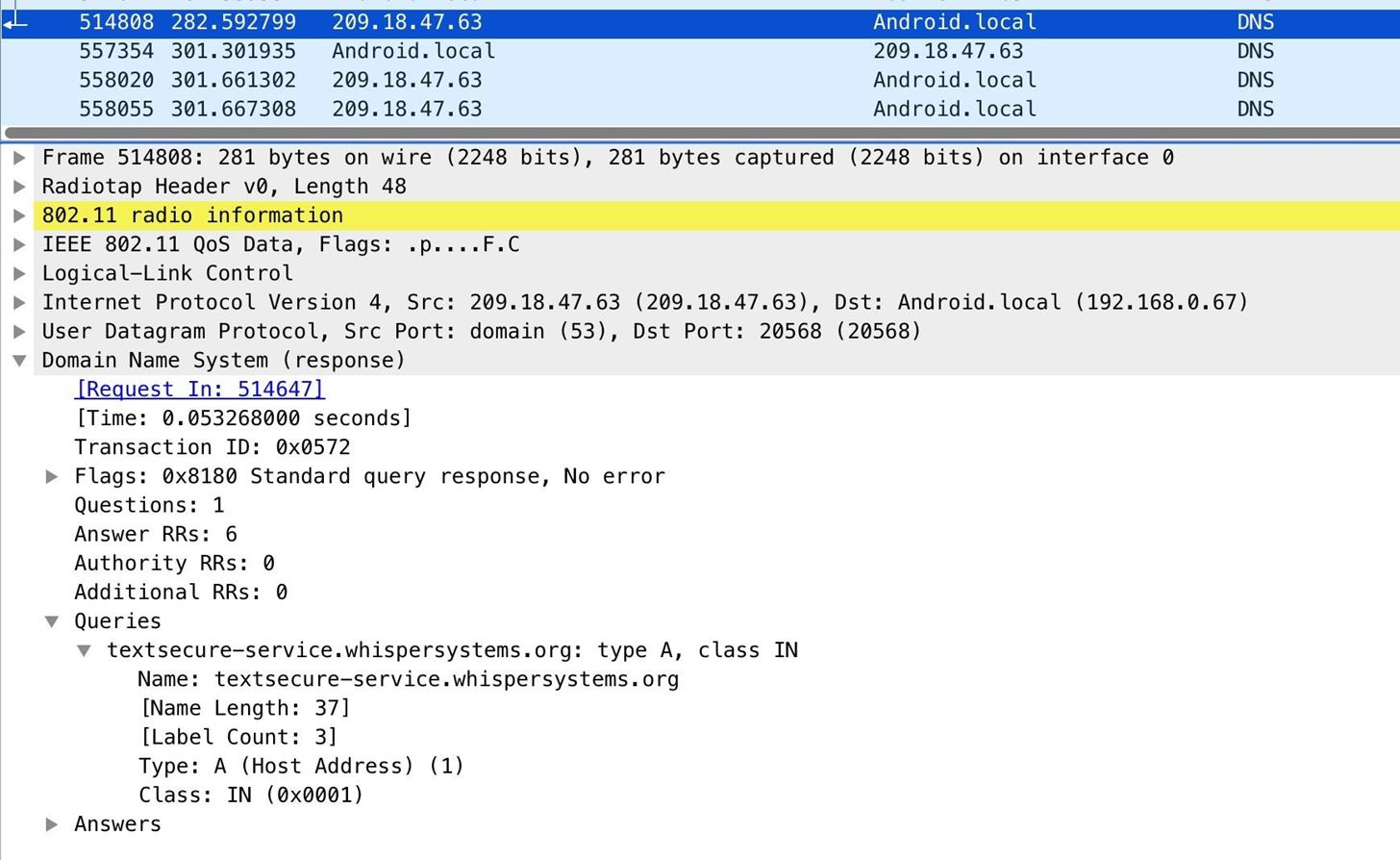
Trying to find that song that'south playing with Shazam leaves the following fingerprint.
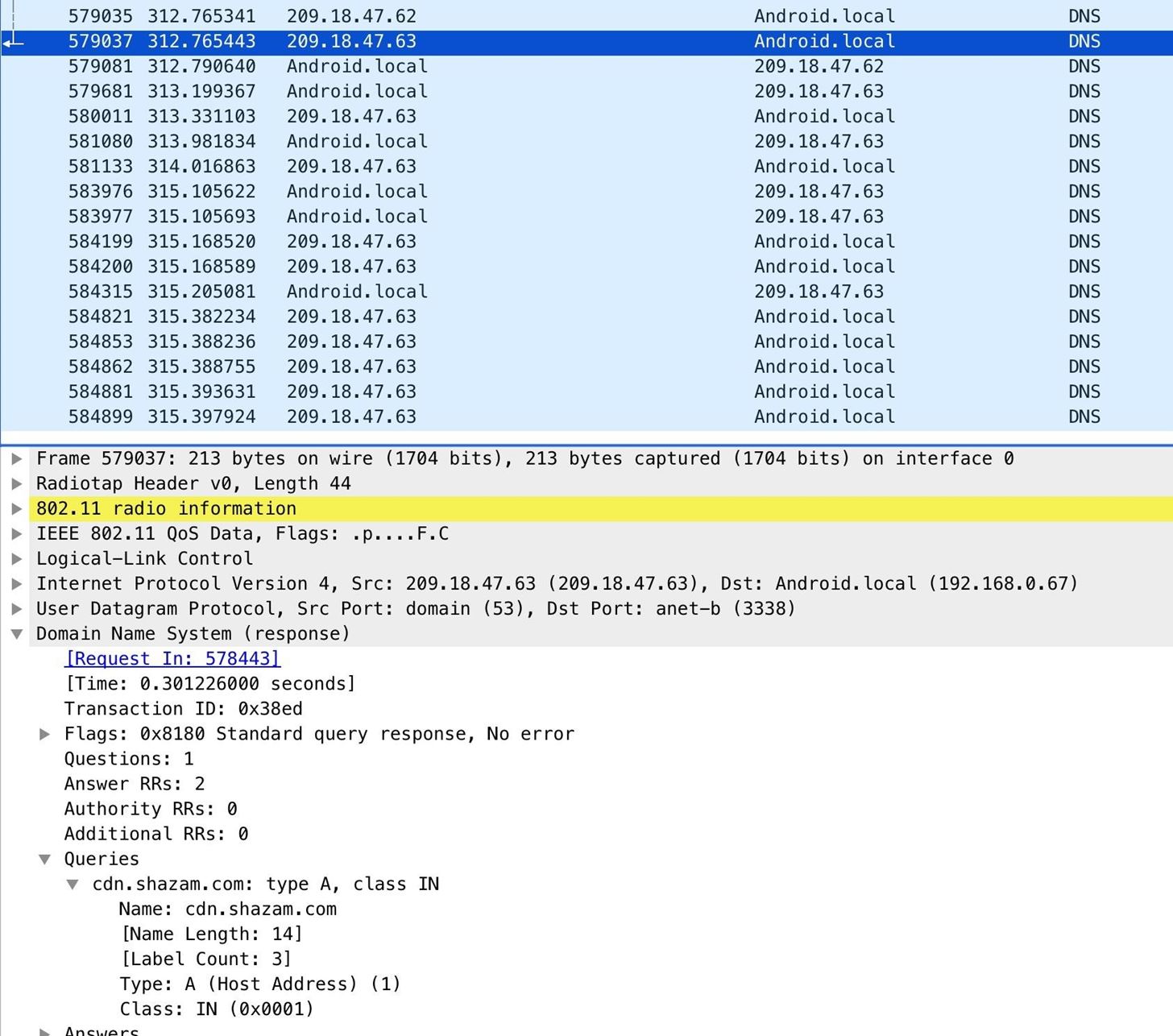
Opening the app to call an Uber creates the requests y'all see below.
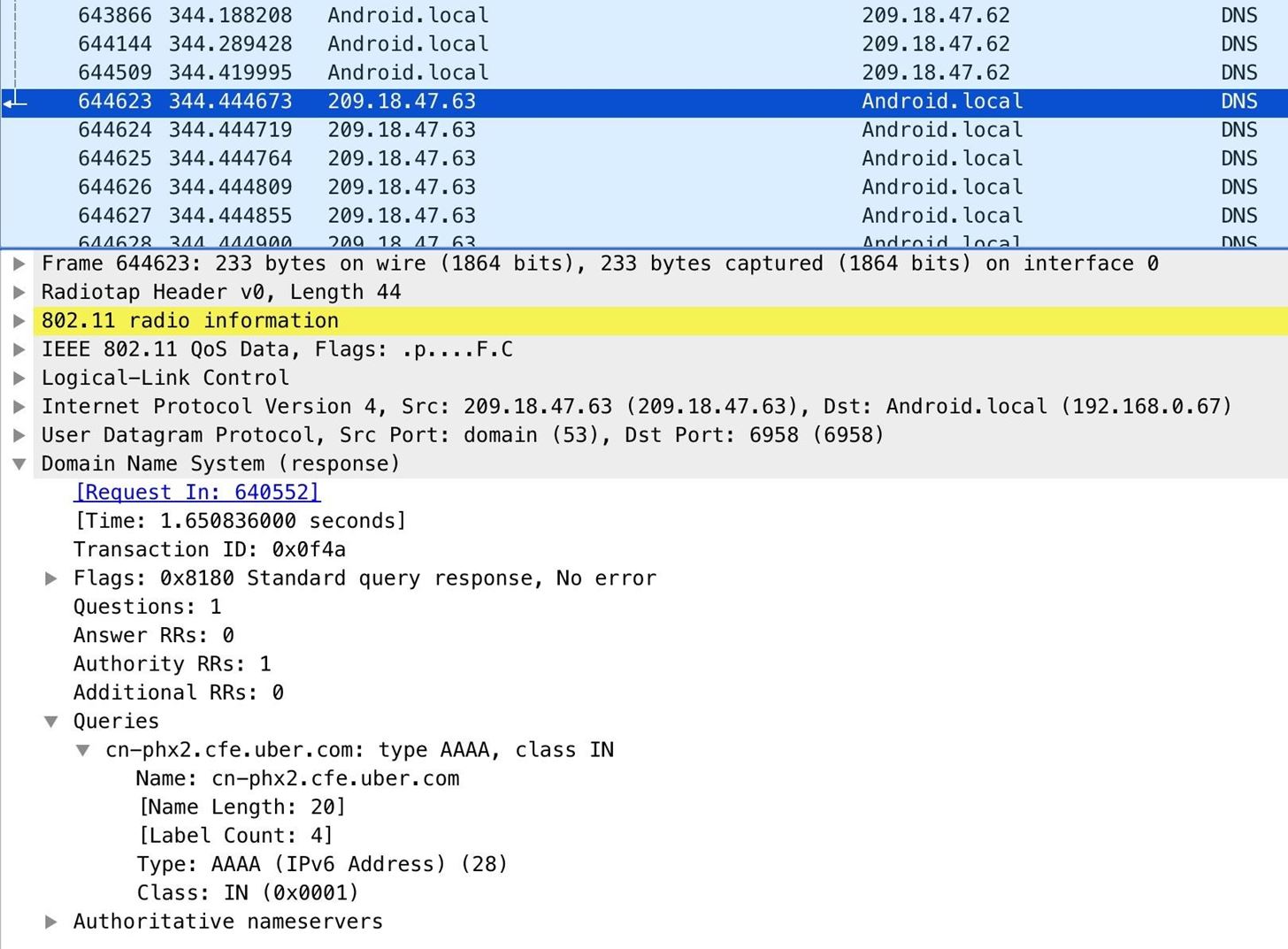
Beneath, we see the effect of opening Venmo, and app for transferring money. It seems like a practiced time to redirect this request elsewhere.
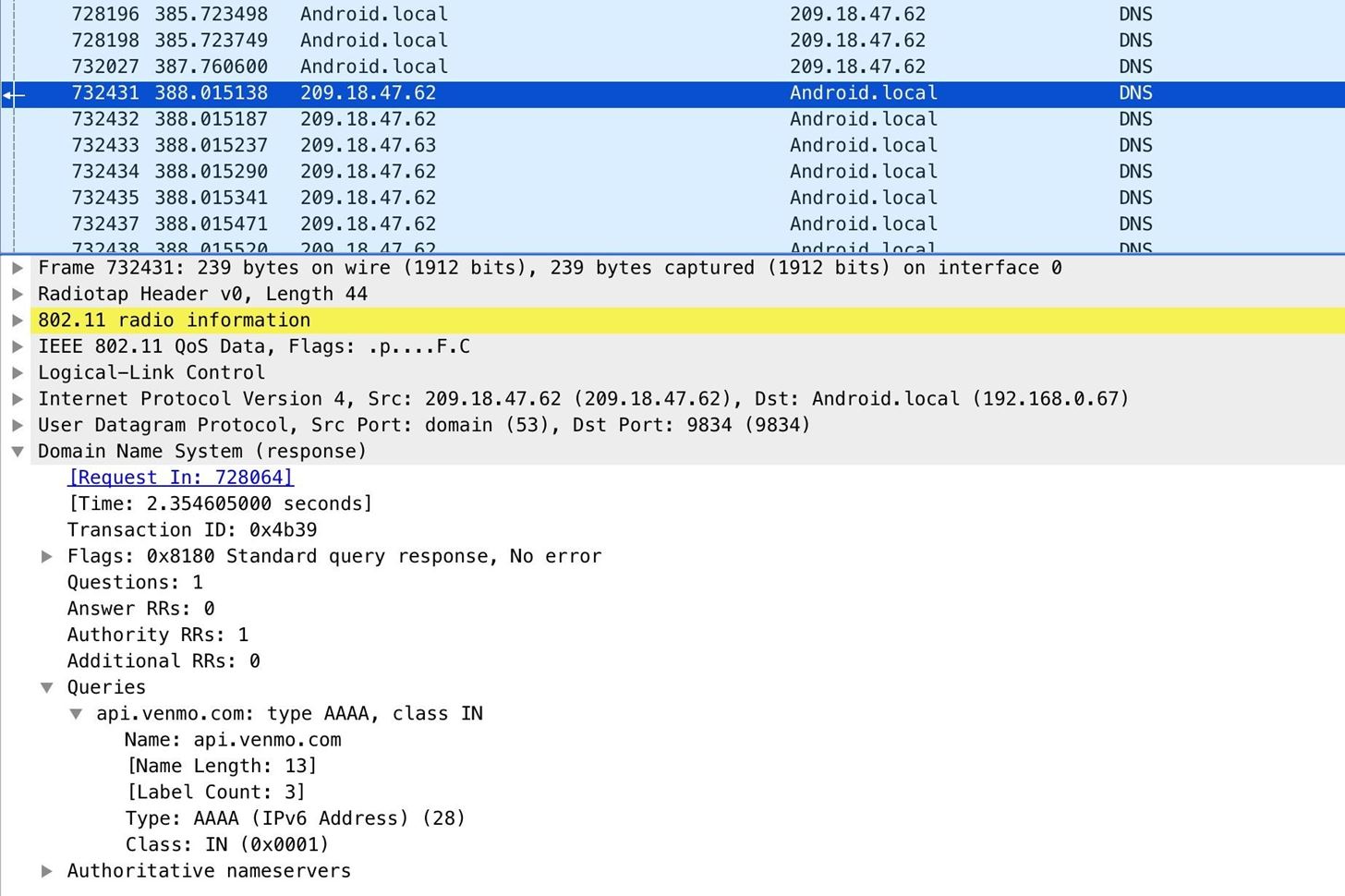
2. HTTP Packets
Side by side upwards, we can come across at that place are several insecure web requests by using the http capture filter. These capture filters comprise information like the useragent, which will tell us the type of device that is connecting. We can examine this by clicking on the packets and expanding the "Hypertext Transfer Protocol" tab.
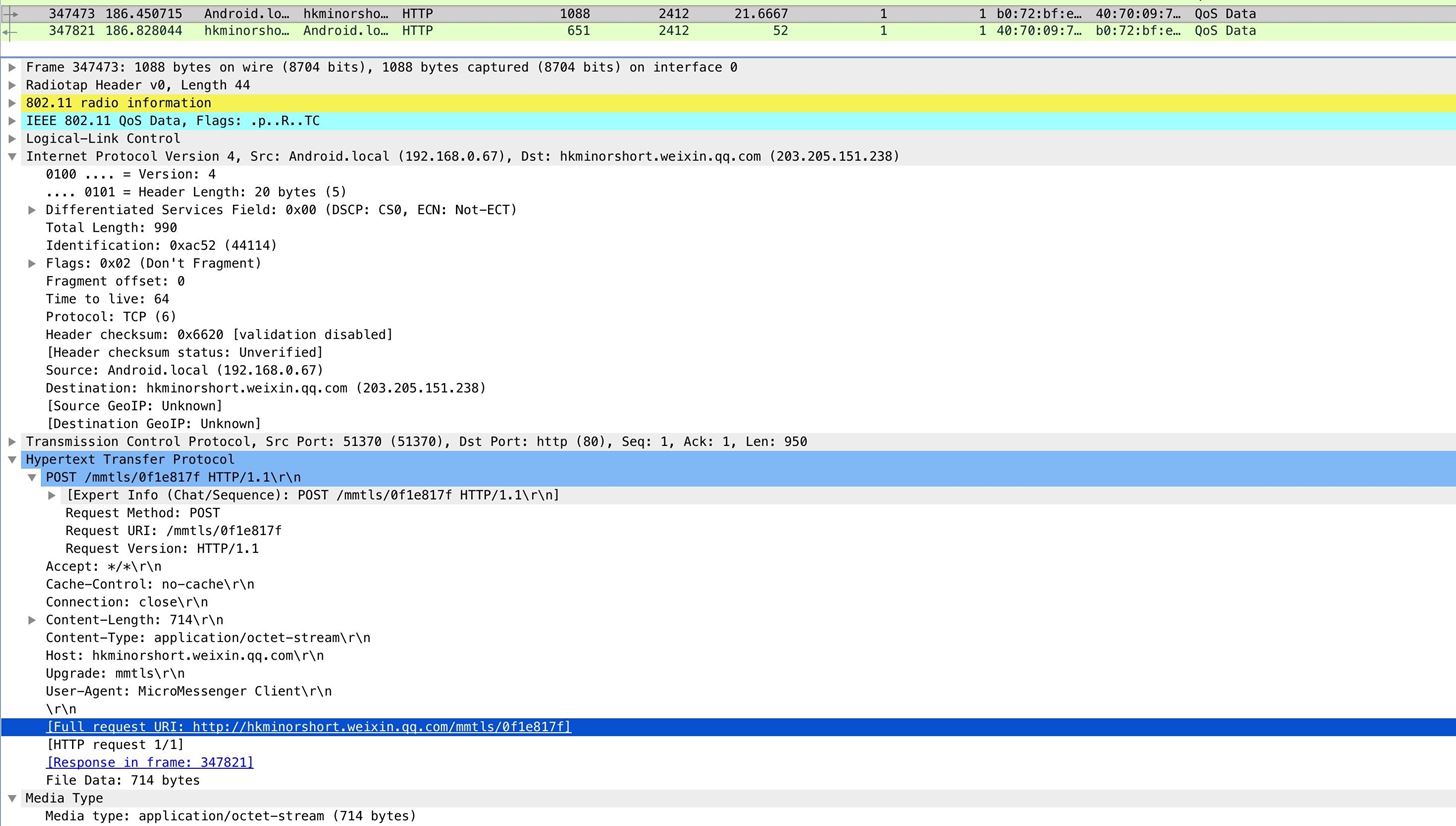
In this example, we can run into insecure HTTP requests to a conversation server. What the heck is this? Merely examining the packet and resolving the domain gives us the answer right away. It's WeChat! This phone has WeChat installed, and further, the communications coming out of it are not entirely encrypted.
If we desire to encounter everything that was resolved, we can click on the "Statistics" carte tab and select "Resolved Addresses" to see all the domains that were resolved throughout the capture. This should be a laundry list of services the device is connecting to via the apps running on it.
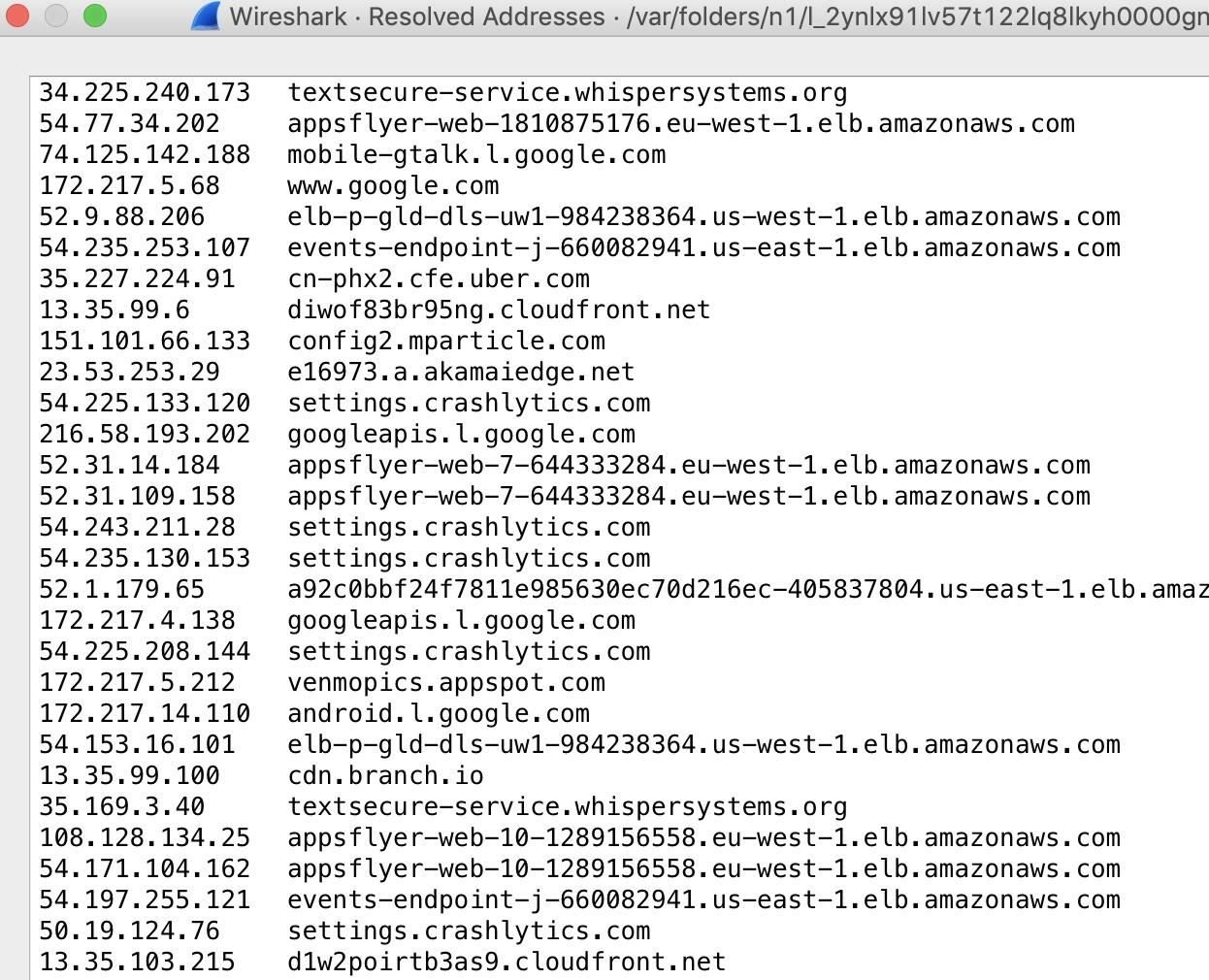
This breakdown makes information technology even easier to run across what the target was up to.
Wireshark Makes Wi-Fi Networks a Risky Thing to Trust
This kind of monitoring may seem invasive, only you should keep in mind that your internet service provider also keeps a log of this information and has the right to sell the data. If you lot want to prevent this kind of snooping, you should get a VPN like Mullvad or PIA that allows y'all to hibernate fifty-fifty local traffic behind potent encryption. In a identify where you might be doing something sensitive over a data connection, you should likewise consider using cellular information whenever possible to prevent this kind of attack.
I hope you enjoyed this guide to using Wireshark to spy on Wi-Fi traffic! If you take any questions virtually this tutorial on Wi-Fi decryption, go out a comment beneath, and feel free to achieve me on Twitter @KodyKinzie.
Want to start making money as a white hat hacker? Bound-outset your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity professionals.
Buy Now (xc% off) >
Other worthwhile deals to check out:
- 97% off The Ultimate 2021 White Hat Hacker Certification Bundle
- 99% off The 2021 All-in-One Data Scientist Mega Package
- 98% off The 2021 Premium Larn To Code Certification Parcel
- 62% off MindMaster Mind Mapping Software: Perpetual License
Source: https://null-byte.wonderhowto.com/how-to/spy-traffic-from-smartphone-with-wireshark-0198549/
Post a Comment for "Can Wireshark Read Https in Monitor Mode"